While most cryptanalysts will tell you that, theoretically, there's no such thing as an unbreakable code, a few cryptographers have created codes and ciphers that no one has managed to crack. In most cases, there's just not enough text in the message for cryptanalysts to analyze. Sometimes, the cryptographer's system is too complex, or there may be no message at all -- the codes and ciphers could be hoaxes.
In the 1800s, a pamphlet with three encrypted messages began to show up in a small community in Virginia. The pamphlet described the adventures of a man named Beale who'd struck it rich panning for gold. Reportedly, Beale had hidden most of his wealth in a secret location and left a coded message leading to the treasure's location with an innkeeper. Twenty years passed with no word from Beale, and the innkeeper sought out help solving the coded messages. Eventually, someone determined that one of the messages used the Declaration of Independence as a code book, but the deciphered message only gave vague hints at the location of the treasure and claimed that the other messages would lead directly to it. No one has solved either of the other messages, and many believe the whole thing to be a hoax.

The Zodiac killer sent ciphered messages like this one to
San Francisco newspapers
in the 1960s.
|
In the mid 1960s, residents of San Francisco and surrounding counties were terrified of a vicious killer who taunted police with coded messages. The killer called himself the Zodiac and sent most of his letters to San Francisco newspapers, occasionally dividing up one long ciphered message between three papers. Allegedly, the ciphers perplexed law enforcement and intelligence agencies, though amateur cryptanalysts managed to crack most of them. There are a few messages that have never been solved, some supposedly a clue to the killer's identity.
Richard Feynman, physicist and pioneer in the field of nanotechnology, received three encoded messages from a scientist at Los Alamos and shared them with his graduate students when he couldn't decipher them himself. Currently, they are posted on a puzzle site. Cryptanalysts have only managed to decipher the first message, which turned out to be the opening lines of Chaucer's "Canterbury Tales" written in Middle English.
In 1990, Jim Sanborn created a sculpture called Kryptos for the CIA headquarters in Langley, Va. Kryptos contains four enciphered messages, but cryptanalysts have solved only three. The final message has very few characters (either 97 or 98, depending on whether one character truly belongs to the fourth message), making it very difficult to analyze. Several people and organizations have boasted about solving the other three messages, including the CIA and the NSA.
While these messages along with many others are unsolved today, there's no reason to believe they will remain unsolved forever. For more than 100 years, a ciphered message written by Edgar Allen Poe went unsolved, puzzling professional and amateur cryptanalysts. But in 2000, a man named Gil Broza cracked the cipher. He found that the cipher used multiple homophonic substitutions -- Poe had used 14 ciphers to represent the letter "e" -- as well as several mistakes. Broza's work proves that just because a code hasn't been solved doesn't mean it's not solvable [source: Elonka.com].
You're the Cryptanalyst
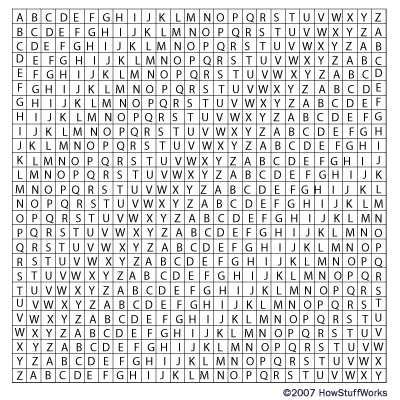
The following message is enciphered text using a method similar to one discussed in this article. There are clues in the article that can help you solve the cipher. It might take you a while to find a method that works, but with a little patience you'll figure it out. Good luck!
KWKWKKRWRKKKKKWRSRWWO
SWWSWORSSRWOROSROKSKWK
OKOKWSOWRSSORWRKWOWKR
KSRKRWKWRWSWRROWRSOKS
KSRSWRKKOOWOOOKSOKKRS
RWRWSWROSKKWRWKKSWKSS
RWOORWRWWSWSSKWSWOWRK
SWSWKWKOKKORKROWSKRRK
WSWWWKWOOROWSKRKSKOWW
Highlight below with your mouse to see the answer:
You have deciphered a code based on the ADFGX cipher used by Germany in World War I. The key word was Discovery.
|
To learn more about cryptology, follow the links on the next page.