Surveillance and Stealth
Explore the technologies used by the military to covertly acquire intelligence and infiltrate enemy lines. Learn how sophisticated listening devices and invisible aircraft enable military forces to get right up to the enemy's doorstep.

Watch Your Six: Military Jet Pictures

McDonnell Douglas F-4 Phantom II

Lockheed P-38 Lightning

Does Army experience help your civilian career?

How NCO Professional Development Ribbons Work

How Army Reconnaissance Jobs Work

How Agent Orange Worked

How Biological and Chemical Warfare Works

How Mustard Gas Works

What Is the Strongest Military in the World?

5 Countries That Ditched Their Military Forces

Coast Guard Rescue Swimmers Risk All to Save Lives

Anatomy of an Underwater Explosion

Can You Really Outrun an Explosion?

How Blast-resistant Clothing Works

HowStuffWorks Illustrated: Two Legal Gun Modifications

Gun Pictures

What's the world's smallest gun?

Are robots replacing human soldiers?

Can drones replace fighter jets?
Do wars drive technological advancement?

Submarine Pictures

How the Zumwalt Class Destroyer Works

How Aircraft Carriers Work
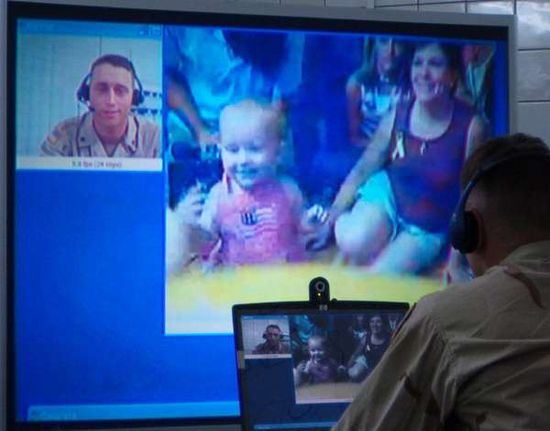
How Military Video Conferencing Works

Why a Draft Would Weaken the U.S. Military

What Was the First War?

Top 5 Gadgets on the High-tech Soldier

YOU Can Drive a Tank!

Is the army testing an invisible tank?

Centurion Main Battle Tank
Learn More
The word ghillie might conjure images of snipers or ghostly figures in thick brush. But its roots go back to Scotland and the River Spey, where ghillies originally served as guides for hunting and fishing.
There is some serious technology and ingenuity involved in making a 172-foot-wide, bomb-carrying aircraft "disappear." Find out how the B-2 bomber deals with enemy radar.
By Tom Harris
On a television drama last week, the plot involved photos taken of a Russian missile silo, and the characters mentioned a "keyhole satellite." What is a keyhole satellite and what can it really spy on?
Advertisement
Gathering reconnaissance during battle typically puts small teams of soldiers in harm's way. Tiny robotic flyers, called micro air vehicles (MAVs), could do away with this danger. Learn all about spy flies.
By Kevin Bonsor
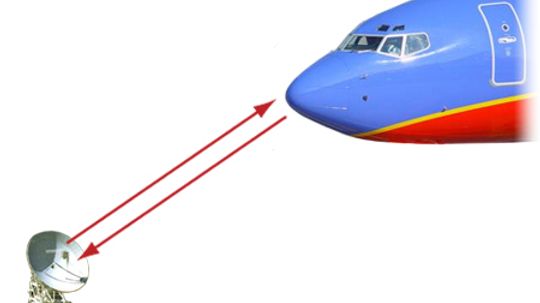
When an airplane is described as a "stealth" aircraft, what does that mean? What is "stealth technology" and how does it work?
Code breakers use logic and intuition to uncover secret information. From ciphers in ancient Greece to modern computer encryption schemes, codes are becoming more complex and harder to solve. Who are the people breaking codes and how do they do it?
We're not talking about one of those laughable get-ups that celebs don when they want to go incognito for a latte. Nope, we're talking elaborate disguises -- from operatic to scientific.